
Cryptolocker and other ransomware is the single biggest threat to your data today. If you are a business, it is doubly as big a threat. I have seen people lose years of their family photos on their home PC, and multi-location corporations all but shut down. This is nothing to take lightly.
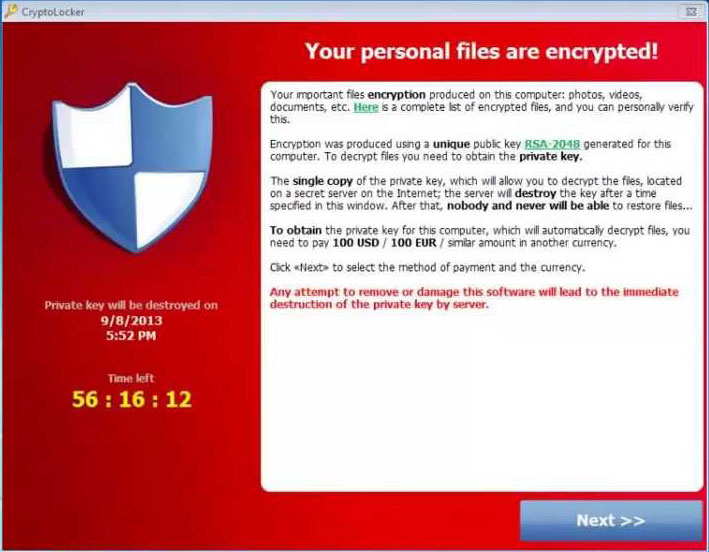
So what is ransomware and how does it work?
Ransomware is a type of malware (unwanted software written by people out to take money from you) that when run on your computer encrypts all of your data (photos, music, videos, documents, spreadsheets, email, etc) so that you can no longer access it. They then give you information on an anonymous way to pay them money for the key to decrypt your data so you can once again access it.
There are two keys needed to decrypt the software, one of which is on your computer and the other is on the bad guy’s server. They give you a certain amount of time depending on the type of ransomware such as a forty eight hours, a week or two weeks to pay the ransom. If you do not pay in the given time then they delete the key off their server and then there is no way to ever decrypt your data.
It can not only affect the data on your computer, but on any mounted drive as well. This includes USB drives, external hard drives, and even shared drives on servers or NAS devices.
Isn’t this illegal? In the United States, absolutely! Unfortunately both the software and payment methods are largely untraceable so there is no way to find that person. Even if you did find them, the odds are they are in a small third world country where what they are doing may not even be illegal.
How widespread is this? Can I just pay the ransom?
Just recently in the news was Hollywood Presbyterian Medical Center that had to pay seventeen thousand dollars because they could not function, all their data was encrypted including patient files, test results and more. The news has also reported several instances of different law enforcement agencies including the Dickson County Sheriff’s Office in Tennessee, the Tewksbury police department in Massachusetts, and the Midlothian Village police department in Illinois being hit by ransomware and paying the ransom.
So what happens if you pay the ransom? The odds are you will indeed get your data back. As much as I hate to say it, if you do not have backups that were not affected this may be your only choice. Without those backups, even the best computer technician most likely will not be able to get your data back.
To my knowledge, very few people have paid the ransom and not gotten their data back. It is said that the companies behind this ransomware (that’s right, this is big business, not some kid in his mother’s basement) have established their own technical support departments to assist people who paid in getting their data back. If people paid and didn’t get their data back, what motivation would people have to pay?
That hospital that was just in the news and paid thousands in ransom, did they get their data back? Yes. All of it? As far as they have said, yes. Some people have heard that some people paid and didn’t get their data back. Yes, and I have heard that the guy down the street was abducted by aliens. The articles about the law enforcement departments above indicate that they too got their data back.
I will say it again, if they did not give you your data back, there would be no incentive for people to pay. They want people to pay, so they tend to fall over themselves making sure you get your data back. If it sounds like I want you to pay them money, that is incorrect. I want you to protect yourself so that you don’t have to.
What about restoring from backups?
A problem with backups is that ransomware can also affect them. If your backup software ran after your files were encrypted, then it backed up useless files. The ransomware could have also encrypted your backups so you can not restore them. The best types of backups are versioned ones (ones that backs up several different copies of each file) and/or ones stored off site. It is also preferable to not use the backup facilities built into your operating system as these are the primary types of backups the ransomware authors will target for encryption.
The best type of backup protection against this would be an automatic cloud based solution such as Carbonite. This software will automatically backup your user data to their servers. Every time a file is changed, it is uploaded to the servers again but that does not overwrite the older version. This way you can restore the file to a state right before it was encrypted and you have lost nothing but a little time.
The next best method is to use a third party backup utility such as Acronis and backup to external hard drives. Once a week or so swap out the drives and keep the one not being used off site or at least in a fireproof safe. Now if you get hit by ransomware you simply restore the data from the day before you were hit. Keeping a copy off site simply protects you against fire and theft as well as ransomware.
What do I do if I get infected?
What should you do if you get infected by the ransomware? The first thing to so is turn off any antivirus or antispyware software you may have. Whatever you do, do not run any kind of scan. The reason is as I told you earlier one of the two keys needed to decrypt your data is stored on your computer. If the antivirus removes this key you can not recover your data even if you pay.
What about taking it to a computer repair shop? Don’t bother, there is nothing they can do once you get infected. Sure, they can remove the ransomware and clean up your PC but it is highly unlikely they can get any of your data back. Their solution will most likely be to delete all your data and return the computer to you. They could also want to just reload your operating system and be sure the ransomware is gone. You can do all of this yourself. If you are unsure call your PC manufacturer (for example Dell or HP) and ask them how to restore the PC to factory.
I keep all my data in the cloud, is it safe? Not likely. A lot of cloud services such as Dropbox, Google Drive and iCloud Drive all show up as drives on your computer. Any drive on your computer is likely encrypted.
If you use an Apple computer you may think you don’t have to worry about this. Sorry, wrong. Just recently the Mac program Transmission was hacked to include ransomware on Mac OS X. When you downloaded the program or updated it on the web, it would also install the ransomware. It is true however that this is far less prevalent on Macs than on Windows computers. I expect that to change since virtually no Macs run antivirus or antispyware software and most of the owners think they are invulnerable to this type of attack. Add that with the fact that Macs are more expensive and the bad guys will assume Macs are easy targets with plenty of cash.
How can I prevent this?
How is ransomware delivered to your computer? How do you get infected? By and large through email attachments. You certainly can get infected from software like the Mac just did, or by drive-by web attacks (infected websites), but those are the exception to the rule. I would guess 99% or more of all ransomware attacks I have seen were delivered by email attachments.
So how can you protect yourself from ransomware? First and foremost, do not open email attachments that may be infected. I use this rule: If I am 99.99% sure that it is a legitimate attachment, that is not good enough and I open it on my iPad first. If the attachment opens on my iPad just fine and it is legitimate, then I open it on my PC if I need to. I only open attachments on my PC first if I am 100% sure the attachment is something I should have been sent, and I was expecting it.
I can not stress this enough, every time you see an attachment are you willing to bet everything stored on your computer that it is legitimate? If the answer is not an instant “yes”, don’t open it. Even a little hesitation, open it on a tablet first.
Next, never download a file you are not sure is safe. Free things on the internet rarely are free. Best case is they may include spyware, malware or PUPs (potentially unwanted software). Worst case is ransomware may be included as it was on the Mac with the software Transmission.
It should also go without saying never download things such as pirated movies, music or software. These are frequently infected. You may think that downloading these on a separate machine with really good antivirus and antispyware protects it. Not so. Many of the people we have seen have had excellent antivirus installed and it acted too late. In addition remember that you are not only putting your machine at risk but potentially every other machine on the same network.
Is there software that will help prevent infection?
Once you take all that advice to heart, on a Windows computer you can download a program called CryptoPrevent. This software was written by Foolish IT and is available from www.foolishit.com. This tool isn’t magical, it simply prevents executable programs from running from places it really shouldn’t. The majority of ransomware runs this way, so this can stop it before it has a chance to encrypt your files.
The CryptoPrevent basic software is free, with paid versions providing automatic upgrades and more features. If you are seriously worried you may do something stupid, I would pay for the pro version and make sure it was always up to date.
The antispyware software HitmanPro has released a piece of software called HitmanPro.Alert which says it will not prevent the infection but will prevent the encryption of your data. The software is available from www.surfright.nl and I believe is $24.95 for one year. It is also licensed in a 3 pack and in a 3 year license. Since this solution uses a completely different approach to ransomware protection it could be effectively used in conjunction with CyrptoPrevent as a two pronged solution.
One caution: I have heard of a few problems with the HitmanPro solution such as software incompatibilities. Since I do not run the software myself, I would suggest you do a quick internet search just to make sure.
No software is a substitute for good ole common sense and backups but it can work well with them to not only keep you out of trouble, but get you out of a jam when everything fails.
Safe surfing!
